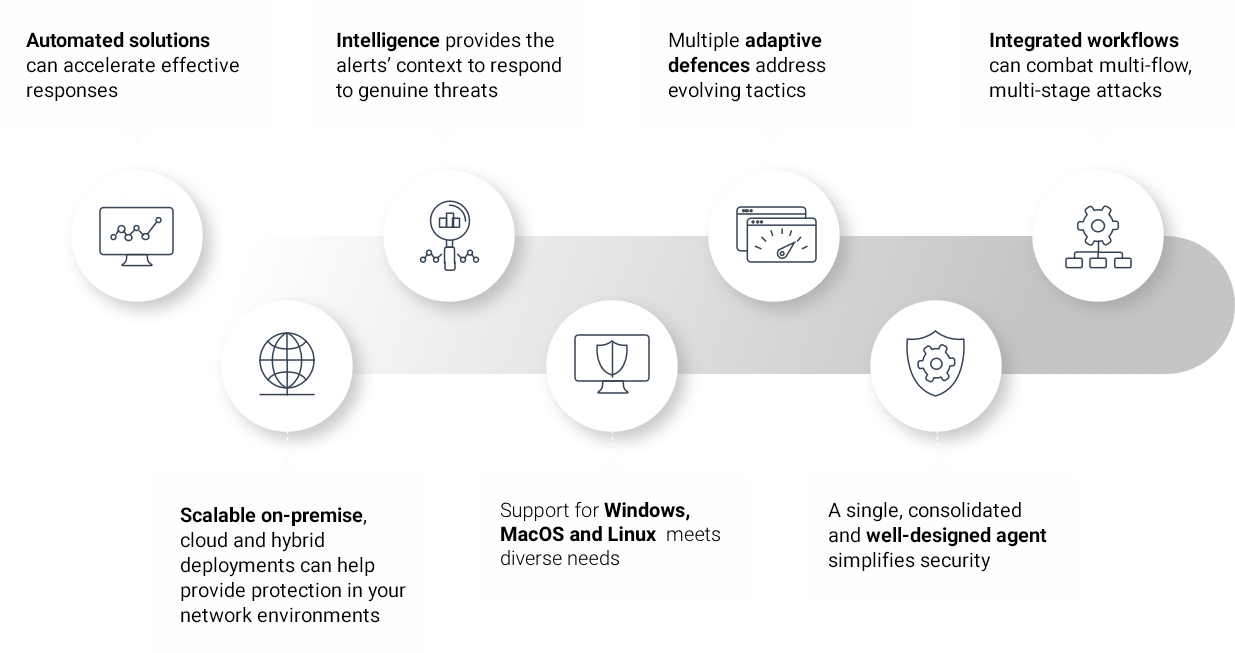
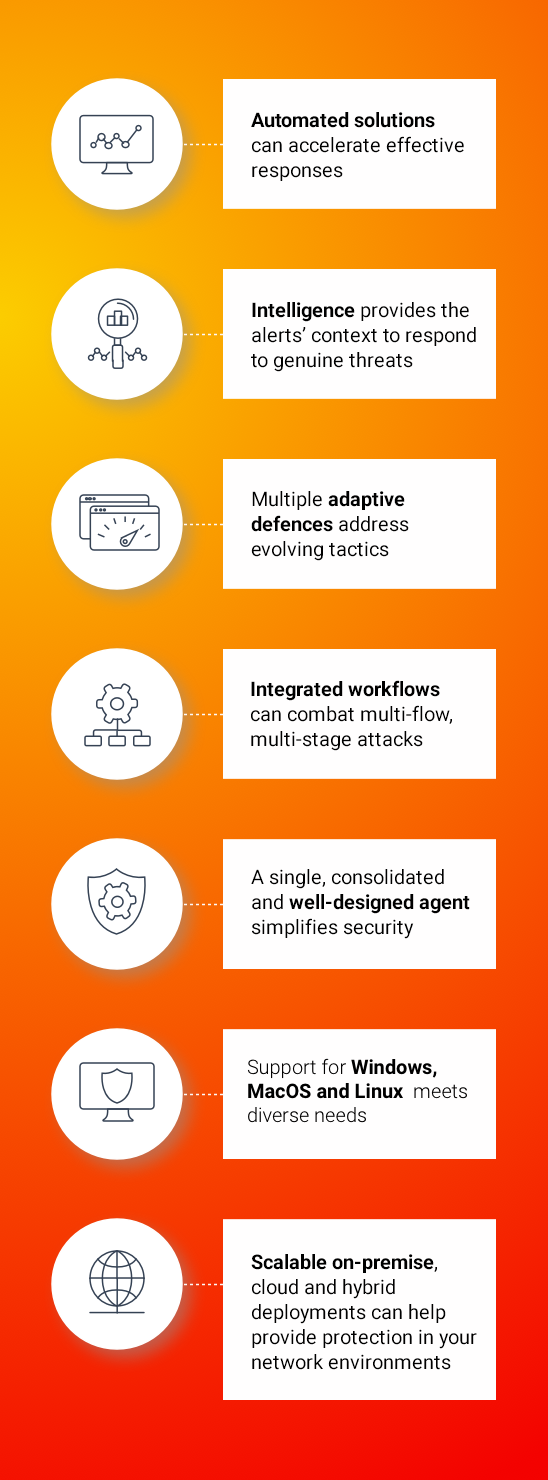
Endpoint Detection and Response
The Endpoint Detection and Response (EDR) platform increases visibility, detection and prevention.
Threat intelligence is refined information about potential or current attacks that threaten an organization. Thanks to the support of our security specialists, the combination of threat intelligence and EDR technology monitors your environment and proactively defends your assets. The EDR solution uses lightweight, discreet monitoring tools designed to be deployed on all relevant Windows, Mac OS, and Linux computers.
Sensors are custom-configured and administered remotely, collecting behavioural data from endpoint devices. They are specifically designed to withstand attacks from adversaries and require very little maintenance.
The EDR console provides a visual layout of affected systems and a timeline of the breach steps to track anomalies, capture trends and detect threats or advanced attack techniques.
Lightweight Multi-Engine Agent
Minimizes configuration and maximizes detection and blocking through a single agent with four detection engines.
Endpoint Protection
Delivers integrated malware protection together with antivirus defences, remediation, behaviour analytics and intelligence.
Enterprise Security Search
Allows to rapidly find and illuminate suspicious activity and threats.
Endpoint Detection and Response
Analyses and responds to threats in a single integrated workflow.
Triage and Audit Viewer
Provides exhaustive inspection and analysis of threats.
Easy-to-Understand Interface
Enables fast interpretation and response to any suspicious endpoint activity.
You Can’t Investigate What You Can’t See. And it’s Next to Impossible to Secure What You Can’t Investigate.
Enterprise networks are dynamic and complex, making it easy for attackers to obfuscate their tracks once inside. As networks grow and expand, it becomes increasingly difficult for security teams to know that network controls are operating and alerts and incidents are being effectively validated and responded to. When all activity is recorded, attackers can no longer hide.
Improve Incident Investigation and Response
When investigating an incident, the response team needs to understand the nature and extent of the compromise, which other systems have likely being interfered with, and the current location of the attacker.
Our advanced EDR tool traces the attacker’s trails and answers these critical questions. By doing so, the response team greatly improves their ability to quarantine and expel the attacker.
Accelerate Alert Triage and the Identification of Malicious Activity
Network analytics tools are effective at catching malicious activity. However, they often lack the contextual information that security analysts need to quickly validate alerts and execute effective responses. EDR adds context by providing a complete record of hosts activity, therefore accelerating the investigation and identification of malicious activity.
EDR solution benefits:
- Increased alerting accuracy resulting in the reduction of false positives
- Comprehensive visualisation of advanced malicious operations
- Near real-time visibility from silent sensors
- Advanced protection through machine learning and behavioural analytics
- Analysts’ action plan to enable rapid remediation